Synopsis
This room will take me through a sample OSINT investigation in which I will be asked to identify a number of identifiers and other pieces of information in order to help catch a cybercriminal.
Platform
TryHackMe
Level
Easy
Walkthrough (with spoilers)
Introduction
Are you ready to begin?
Tip-Off
What username does the attacker go by?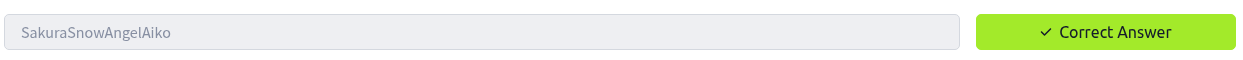
Image provided: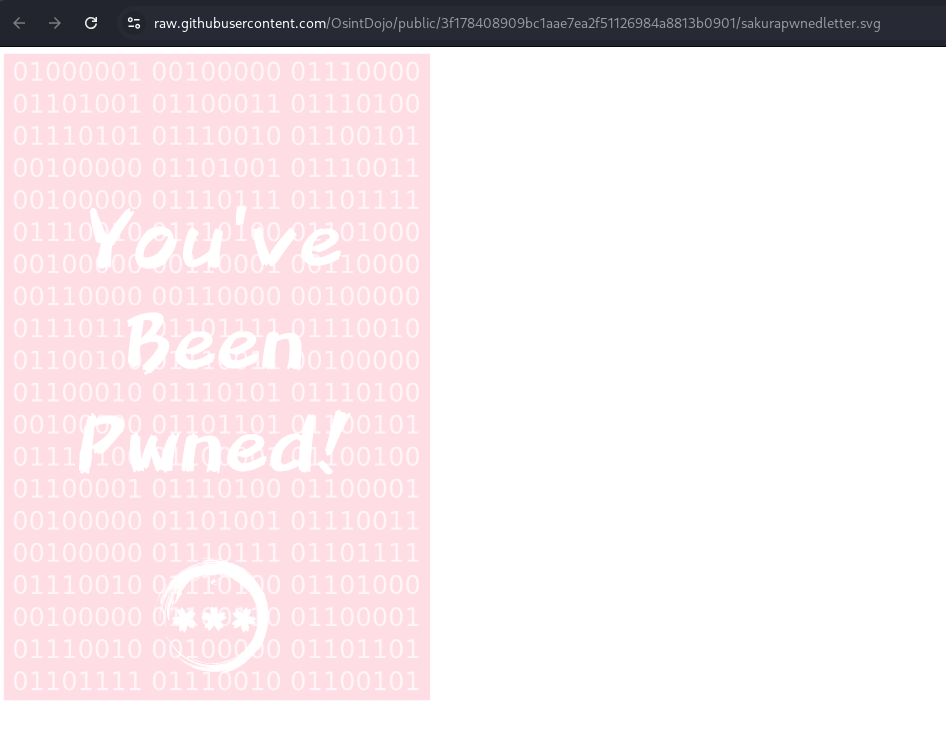
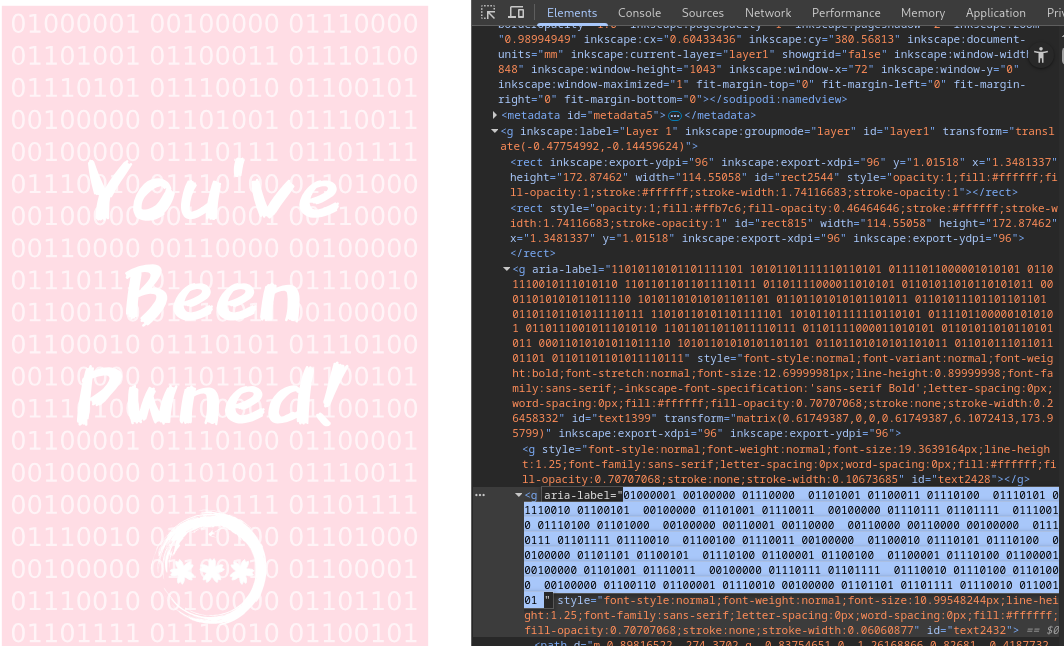
I noticed binary code embedded in the image and was curious about its message. After converting it to text, it revealed: 'A picture is worth 1000 words, but metadata is worth far more.'
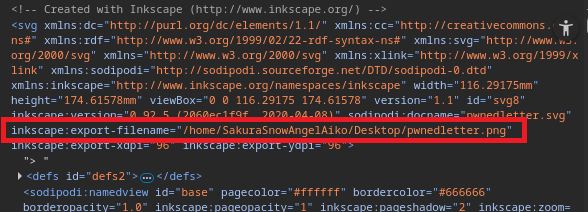
I also discovered a file path: /home/SakuraSnowAngelAiko/Desktop/pwnedletter.png, which led me to believe that SakuraSnowAngelAiko may be the attacker's username.
Reconnaissance
What is the full email address used by the attacker?
What is the attacker's full real name?
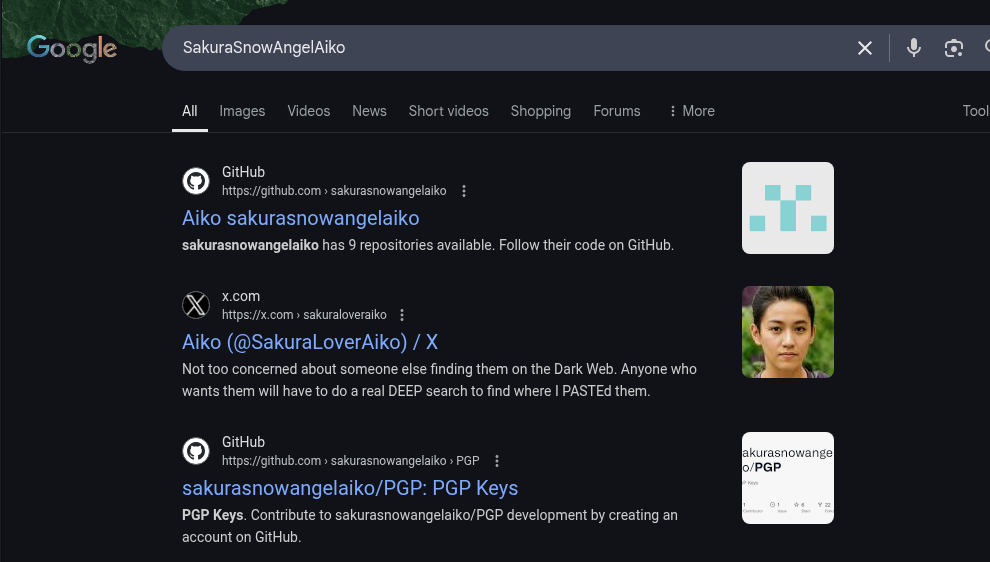
I started by searching "SakuraSnowAngelAiko" on Google. While there were many results, three stood out:
- GitHub: github.com/sakurasnowangelaiko
- Twitter: x.com/SakuraLoverAiko
After browsing both profiles, I couldn’t find any email address. I also checked LinkedIn, but came up empty. Returning to the GitHub profile, I eventually found a PGP public key. It might be a long shot, but I decided to try decoding it using this GPG decoder.
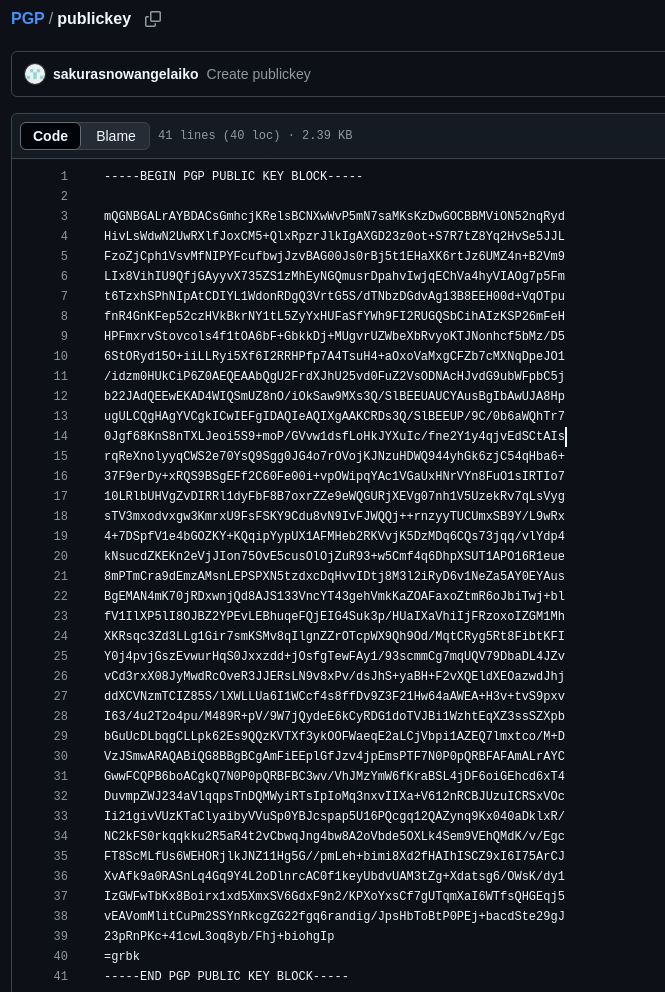
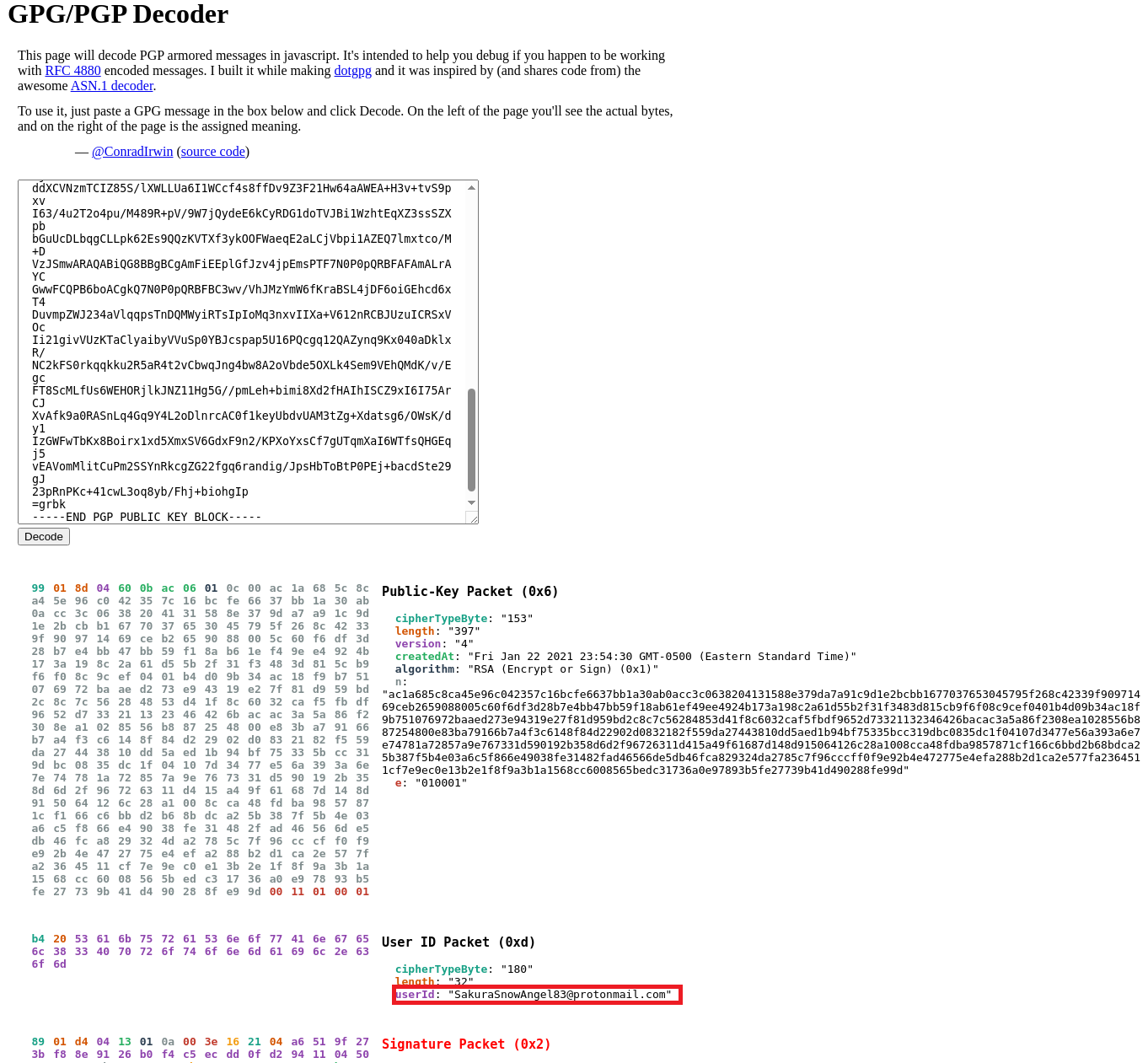
Found his email address!!!
Next, I set out to find his full name. Since I had already searched through GitHub, Twitter, and LinkedIn, I was able to uncover it with ease.
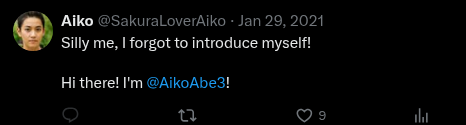
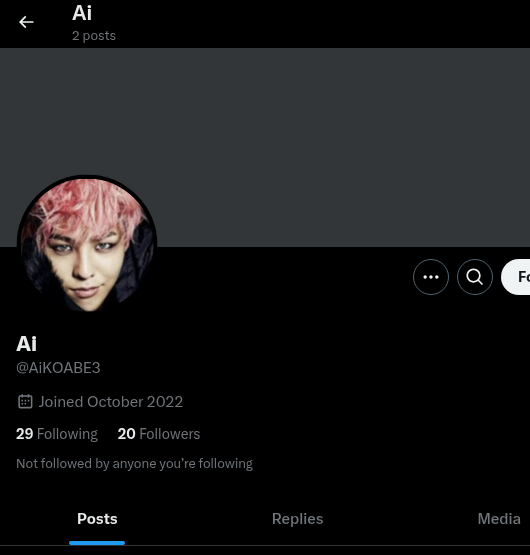
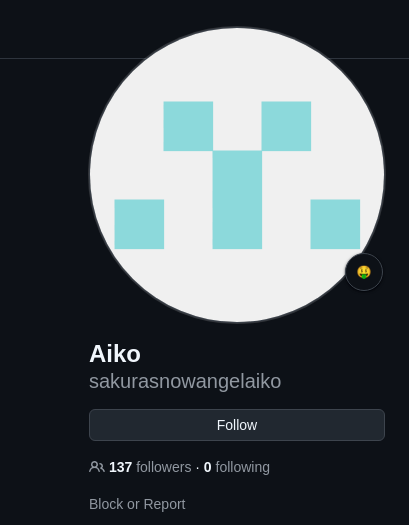
Unveil
What cryptocurrency does the attacker own a cryptocurrency wallet for?
What is the attacker's cryptocurrency wallet address?
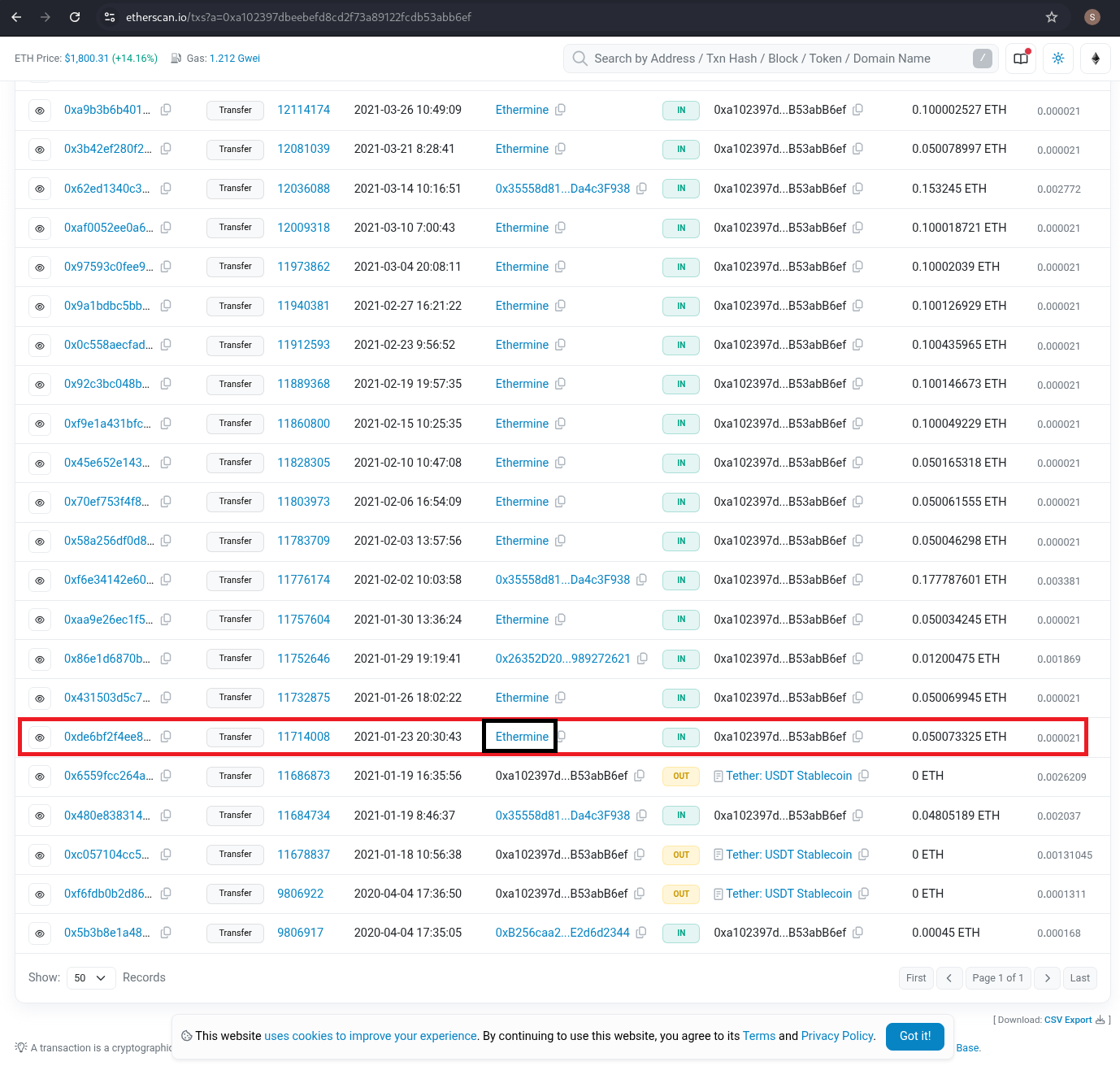
What mining pool did the attacker receive payments from on January 23, 2021 UTC?
What other cryptocurrency did the attacker exchange with using their cryptocurrency wallet?
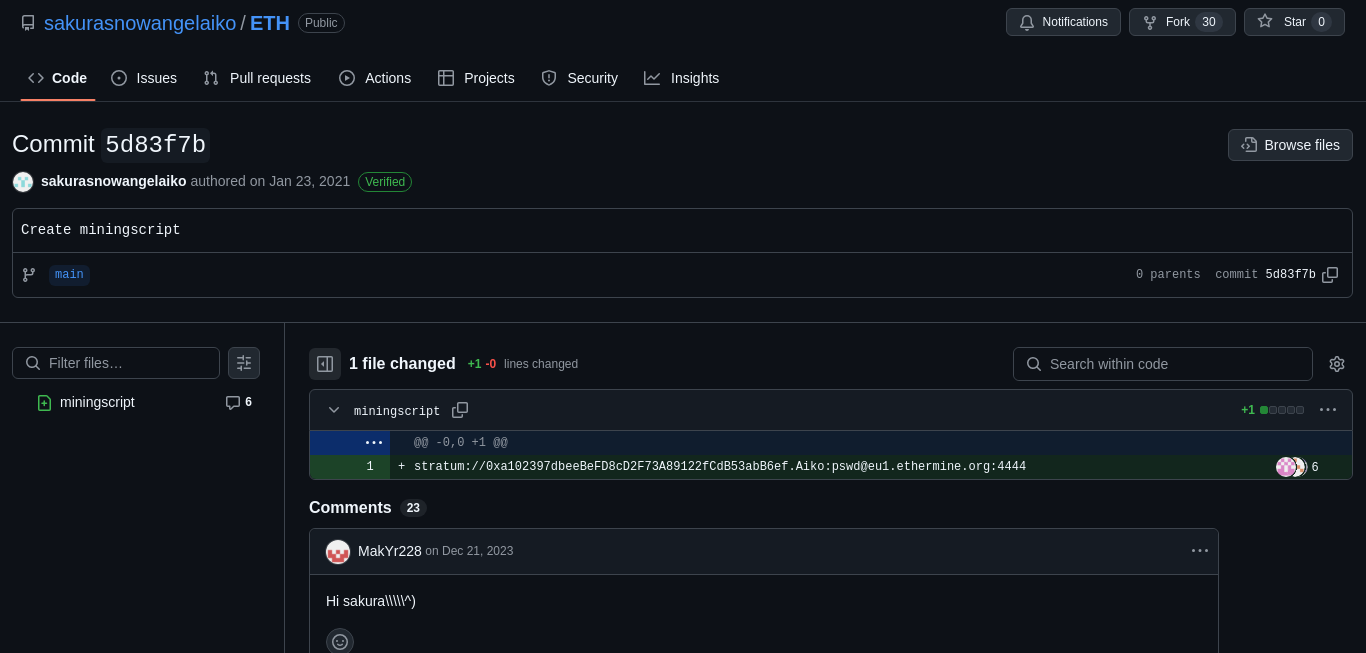
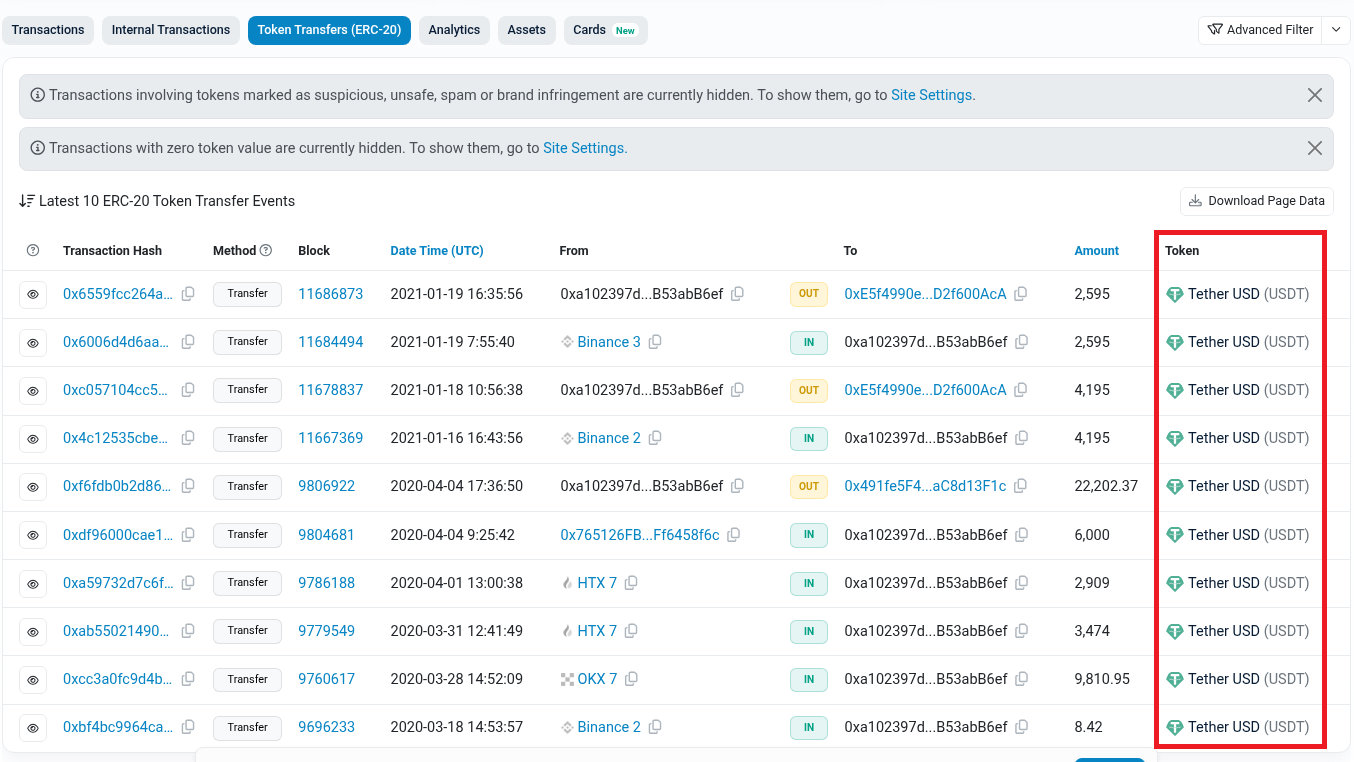
While browsing through the user's GitHub, I discovered nine repositories. The ones that stood out most were related to Ethereum (ETH) and Bitcoin. Within the ETH repository, I found two commits. Upon reviewing them, I was able to identify the user's wallet address, the type of cryptocurrency associated with it, and the mining pool being used.
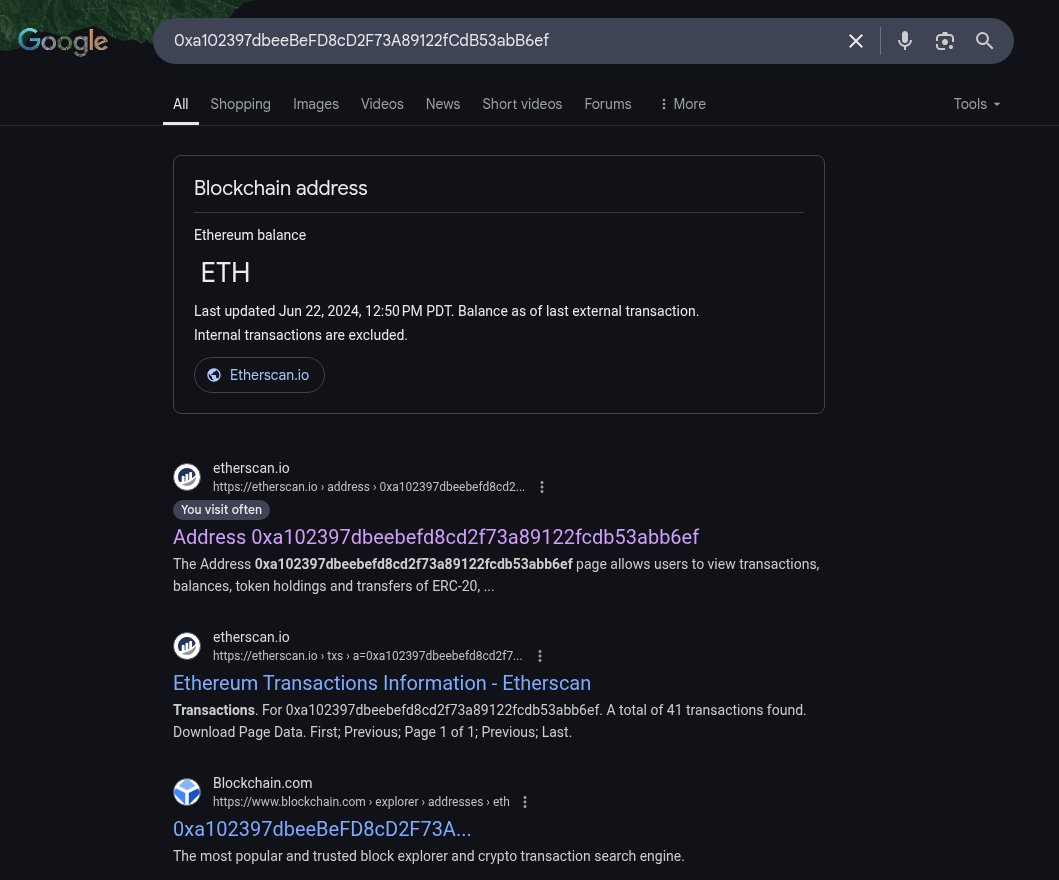
I searched for his wallet address on Google and these were the results:
Taunt
What is the attacker's current Twitter handle?
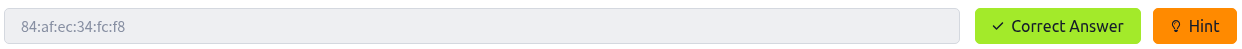
What is the BSSID for the attacker's Home WiFi?
I found his Twitter handle during my initial investigation, which made answering this question straightforward.
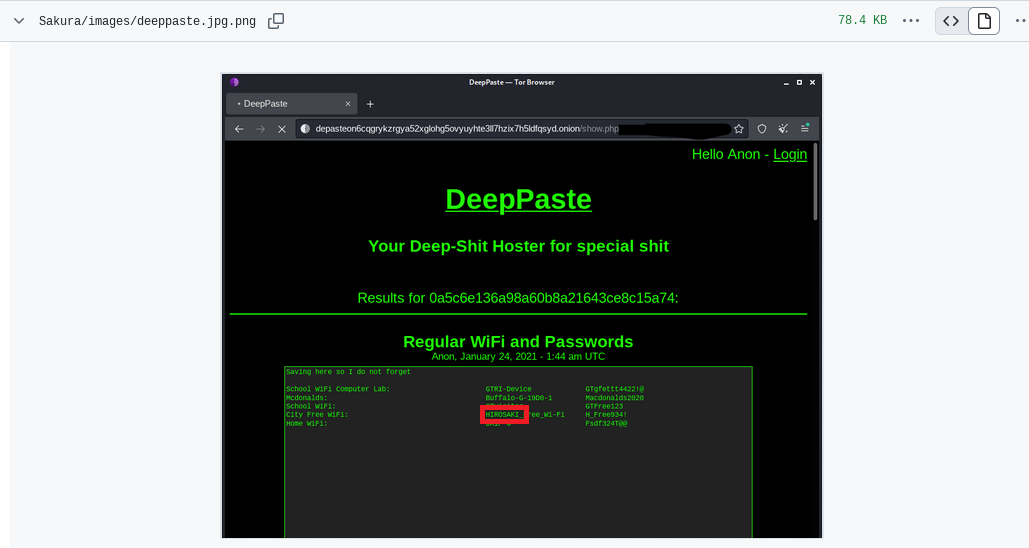
When tackling the next question, I recalled some pictures he had posted that appeared to show potential Wi-Fi names and passwords. Since a BSSID is essentially the MAC address of a Wi-Fi network, my attention was immediately drawn to this information.
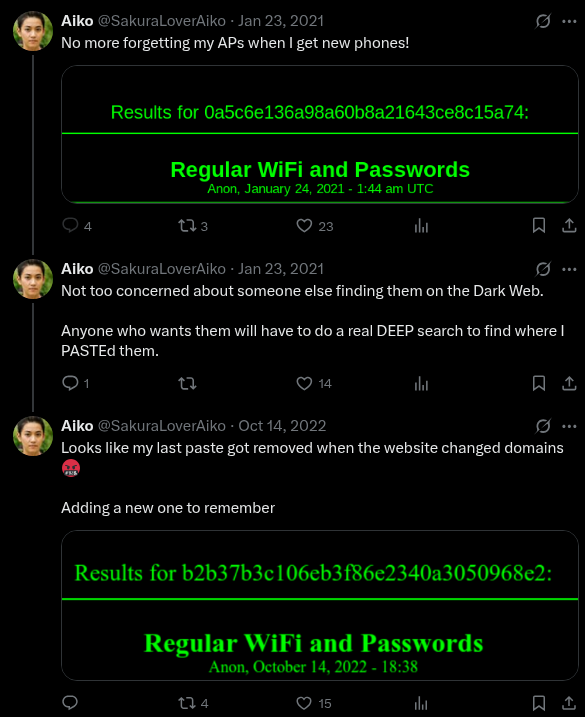
I also noticed that in his response, he mentioned the terms "DEEP" and "PASTE." A quick Google search led me to discover that this likely refers to sites found on the Deep Web, such as paste sites where information is often dumped. I also checked Google Images and found that some of the visuals matched the style of the images he posted on Twitter.
I then accessed the Tor network to search for DeepPaste. During my search, I came across a page that contained a link directing me to the DeepPaste site.
When attempting to access the link, nothing shows up.
Here are the links that I tried:
- http://depastedihrn3jtw.onion/
- http://depasteon6cqgrykzrgya52xglohg5ovyuyhte3ll7hzix7h5ldfqsyd.onion/
- http://deepv2w7p33xa4pwxzwi2ps4j62gfxpyp44ezjbmpttxz3owlsp4ljid.onion/
I spent about an hour trying to track down the new domain, but eventually decided to skip ahead to the next questions while keeping this one in mind. Over the next few days, I kept checking but still couldn’t locate the updated domain—looks like it changes frequently. Eventually, I came across a screenshot on GitHub from a random user showing the contents of DeepPaste using the MD5 hash shared on Twitter. Not ideal, but I’ll take what I can get lol.
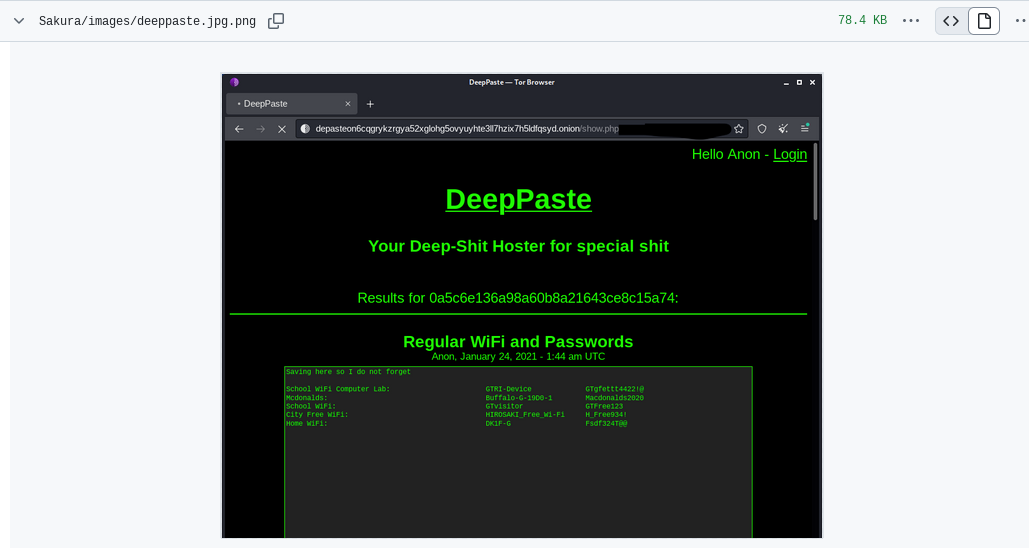
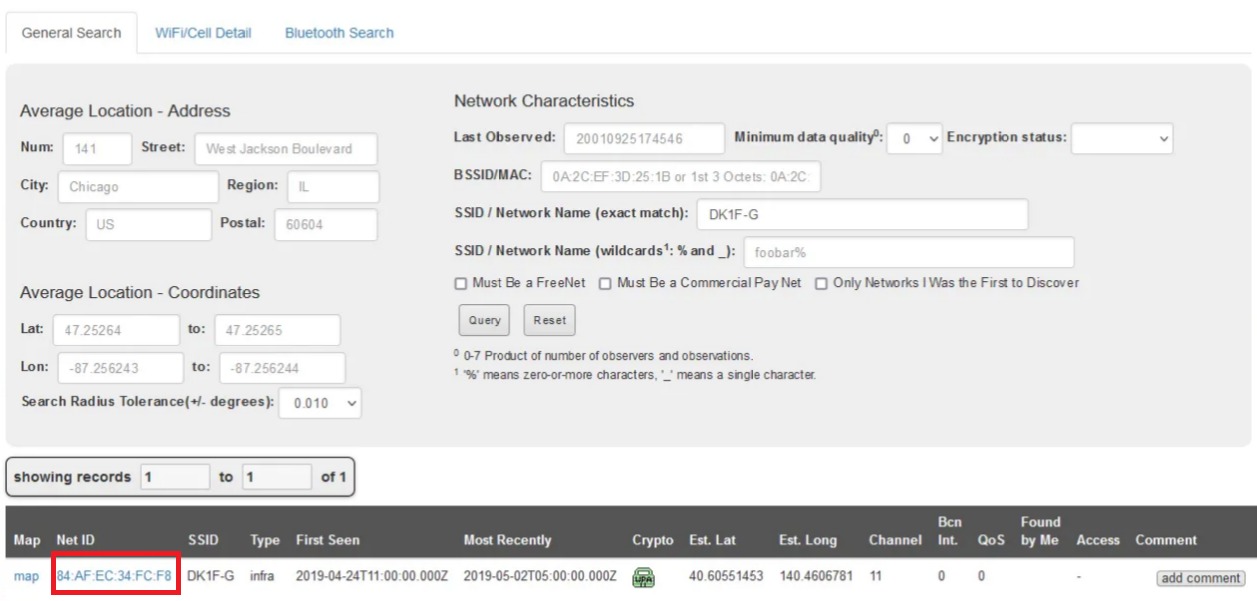
Since the question was asking for the BSSID of the home Wi-Fi, I used wiggle.net to retrieve it.
Homebound
What airport is closest to the location the attacker shared a photo from prior to getting on their flight?
What airport did the attacker have their last layover in?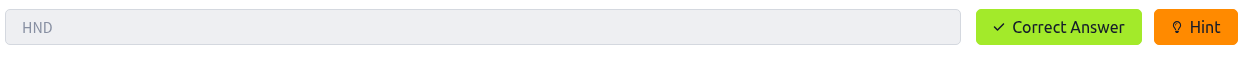
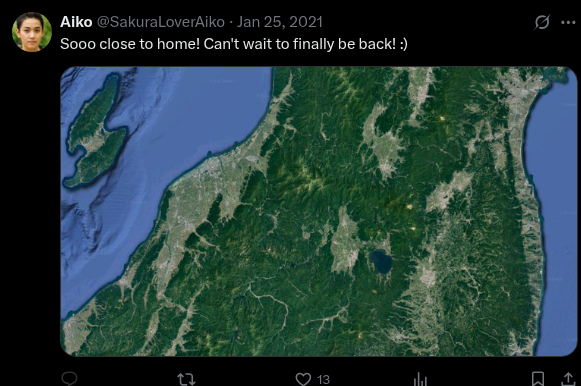
What lake can be seen in the map shared by the attacker as they were on their final flight home?
What city does the attacker likely consider "home"?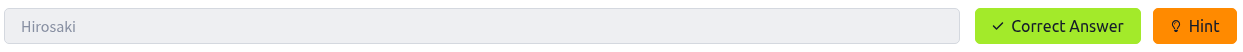
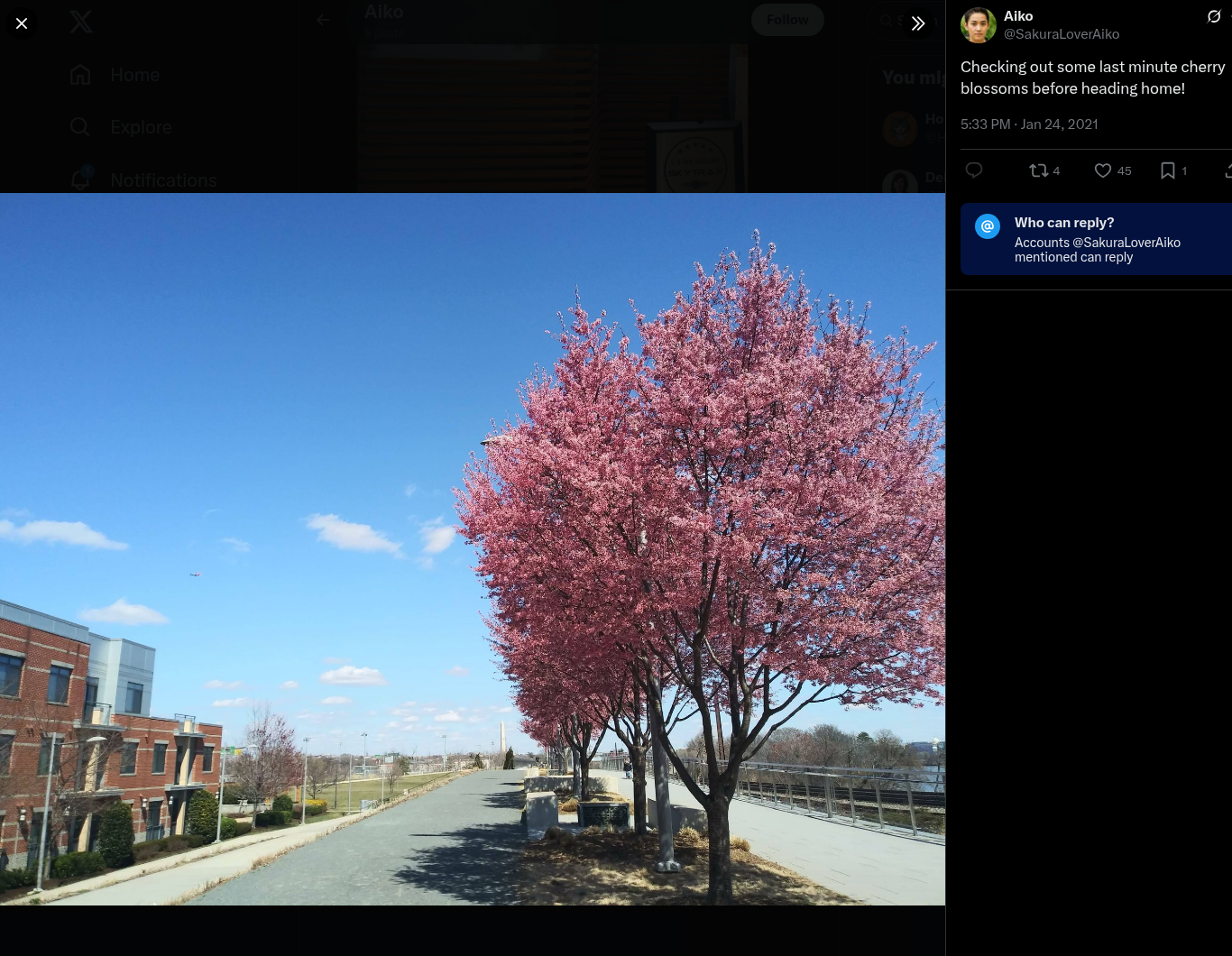
Based on the photo from Twitter, I noticed a structure in the background resembling the Washington Monument. I did a quick Google search and found this:
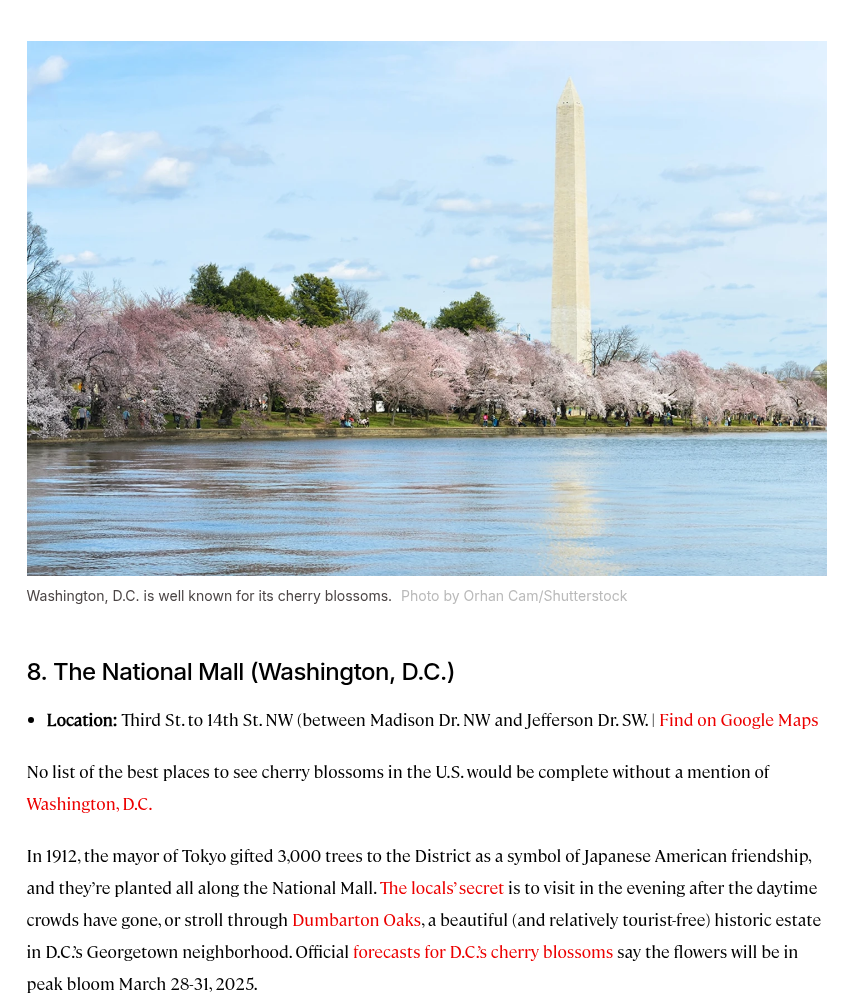
Next, I searched for the closest airport to The National Mall and found this:
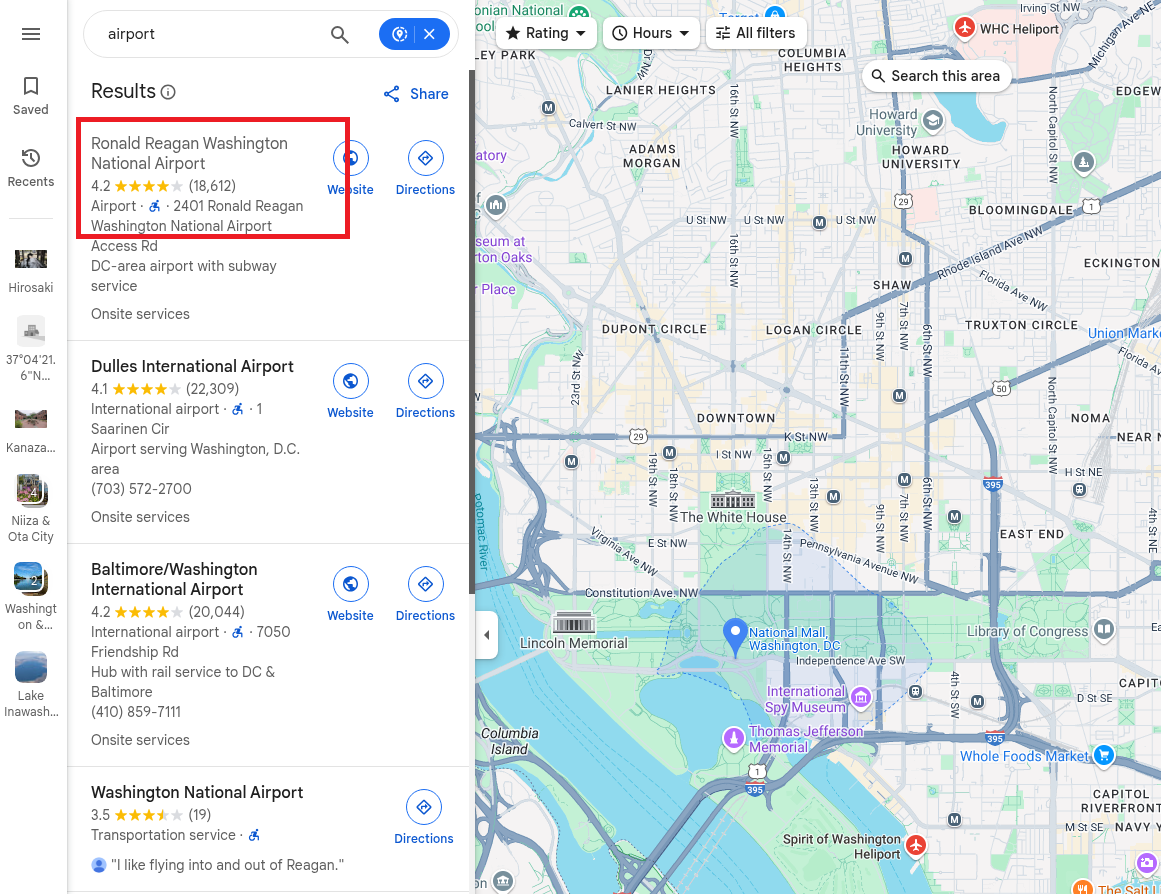
Next, I focused on finding which airport he had a layover at.
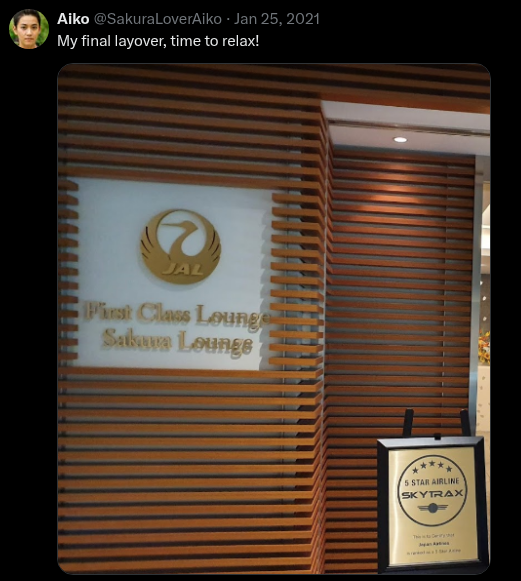
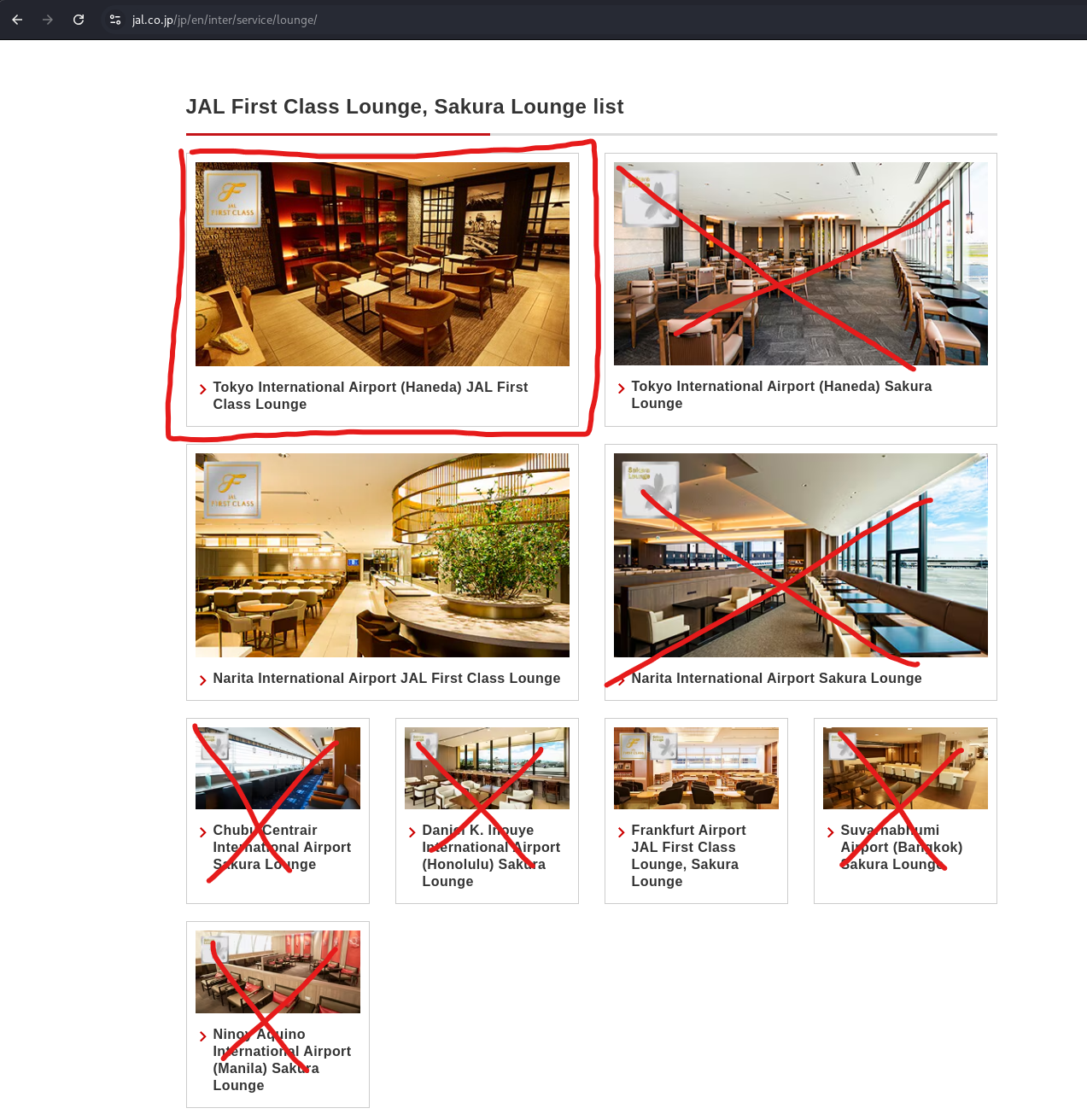
I searched for "First Class Lounge Sakura Lounge" on Google and found this website: https://www.jal.co.jp/jp/en/inter/service/lounge/. The site lists nine lounges, and using the process of elimination based on the image mentioning "First Class," I narrowed it down to three lounges. It turned out to be the first one on the list.
Next, I focused on identifying the lake in the third photo on Twitter. I used Google Maps to pinpoint its location.
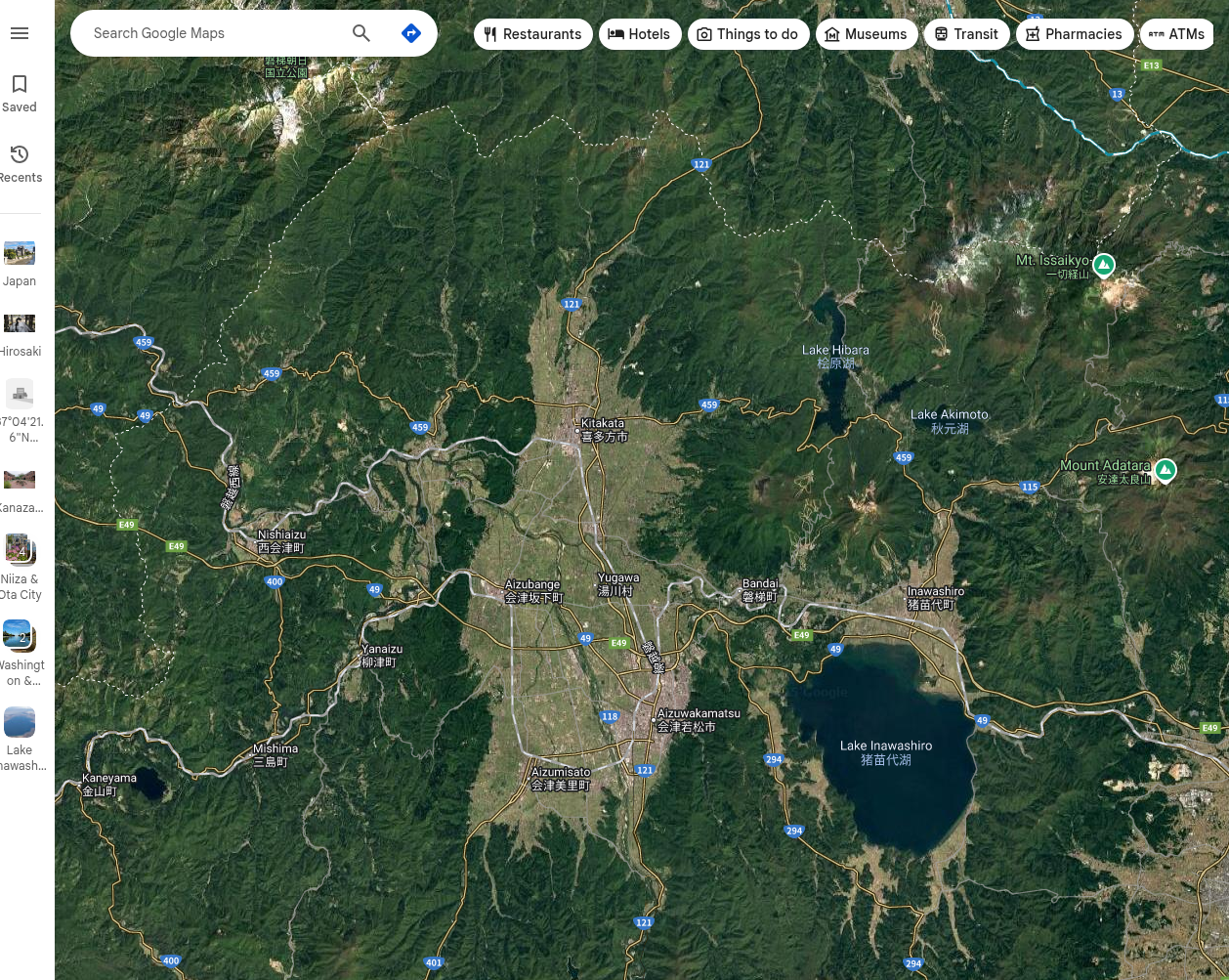
The final question asked for the city where he resides. After some frustration and guessing random cities, I revisited the clues from all sections. The answer was hidden in a DeepPaste screenshot, which mentioned "City Free Wifi."
Lessons & Skills Gained
Through this investigation, I learned the importance of methodical research and connecting disparate pieces of information. By leveraging search engines, social media platforms, and specialized tools, I was able to follow a trail that led from binary code in an image to a deeper understanding of the subject’s digital footprint. This exercise also reinforced the value of persistence in cyber investigations, as well as the need for thorough review of all available clues, even when the solution doesn’t seem apparent at first.
This investigation allowed me to enhance my skills in digital forensics, OSINT (Open-Source Intelligence) gathering, and advanced searching techniques. I gained proficiency in extracting useful information from various platforms like GitHub, Twitter, LinkedIn, and Deep Web resources such as DeepPaste. I also honed my skills in analyzing metadata, identifying hidden patterns, and correlating seemingly unrelated data. Furthermore, the exercise taught me how to utilize geo-locating techniques and resources like Google Maps to track down relevant geographic details.
Honestly, if I hadn’t stumbled upon that screenshot on GitHub from a random user showing the contents of DeepPaste using the MD5 hash, I would have likely hit a dead end and resorted to following a walkthrough article. I’m glad I persisted and didn’t give up, even though I was feeling frustrated.