Summary
Cyber threats continue to evolve, and phishing remains one of the most effective social engineering tactics used by attackers. To better understand and mitigate this threat, I conducted a phishing attack simulation designed to assess user awareness and response to deceptive emails. I invited 10 participants, including family and friends, to take part in this simulation, aiming to strengthen their knowledge of phishing attacks. By exposing them to realistic phishing scenarios, I sought to enhance their ability to recognize and respond to potential threats, ultimately improving their overall cybersecurity awareness.
Objective
The goal of this project was to simulate a realistic phishing attacks to evaluate security awareness and provide educational insights on how to recognize and avoid phishing attempts.
Process
Deploy Gophish
AWS Setup
Created Virtual Private Cloud (VPC), Subnet, Routing Table, Internet Gateways, Security Group, and Key Pair.
Domain Name
- Purchased a domain name through IONOS.
- Configured the A and CNAME records to successfully connect the domain name to the Gophish instance.
- Created a Hosting Zone with Route 53 in AWS.
- Accessed the instance via SSH using an AWS key pair. Generated new SSL/TLS certificates with ACME and configured the admin console and landing pages to utilize the updated certificates for secure connections.
Sending Profile (SMTP Server)
- Setup Amazon Simple Email Service (ASES)
- Created the necessary DKIM and DMARC records to ensure email validity and authentication by properly configuring the required CNAME, MX, and TXT records.
- Linked SMTP credentials to ASES sending profile.
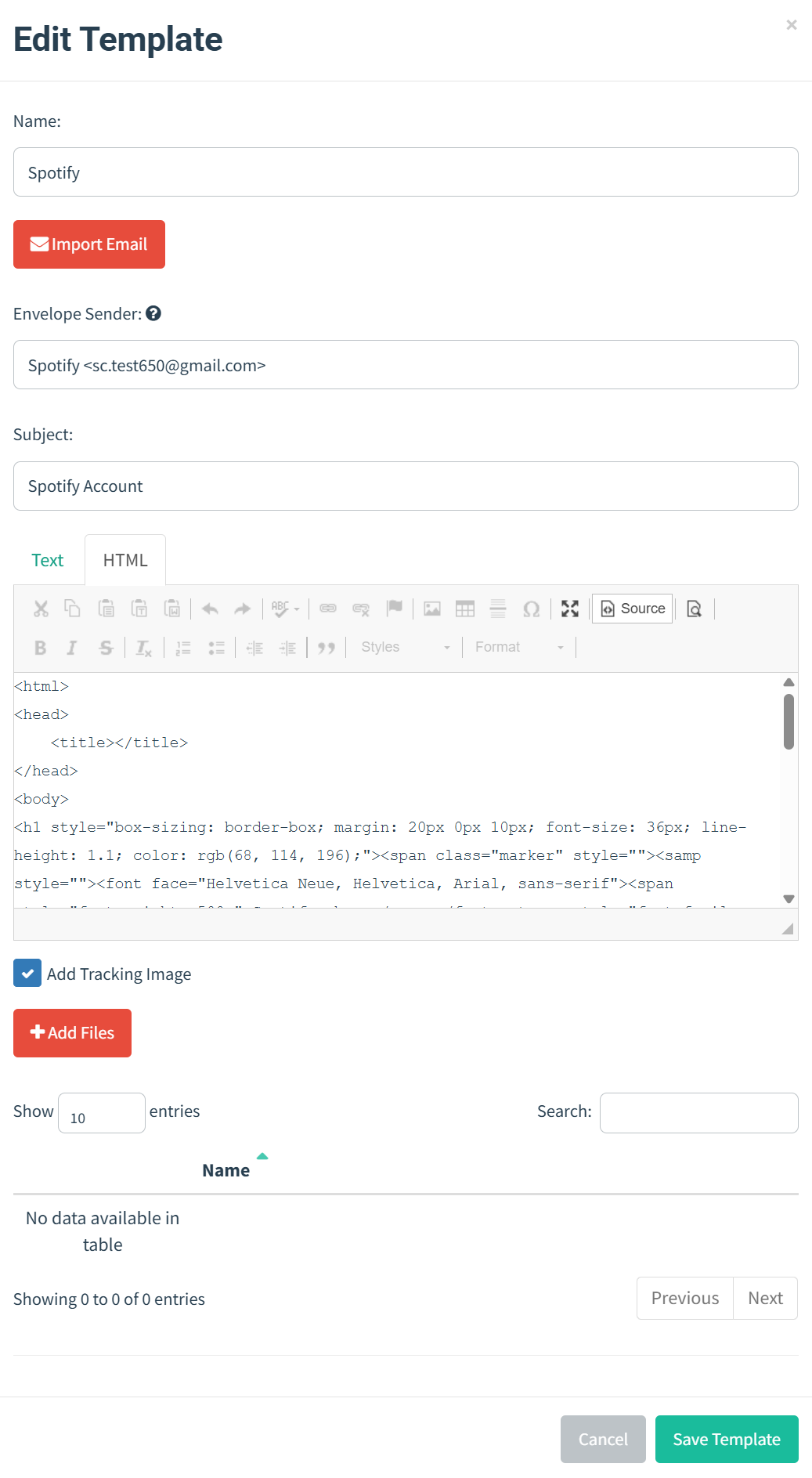
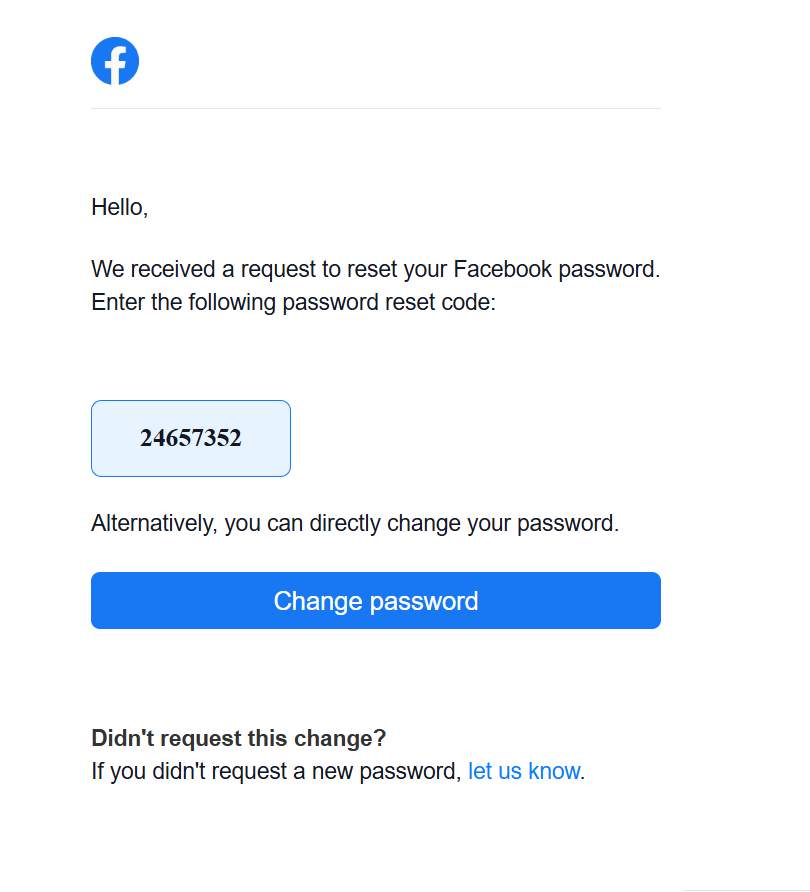
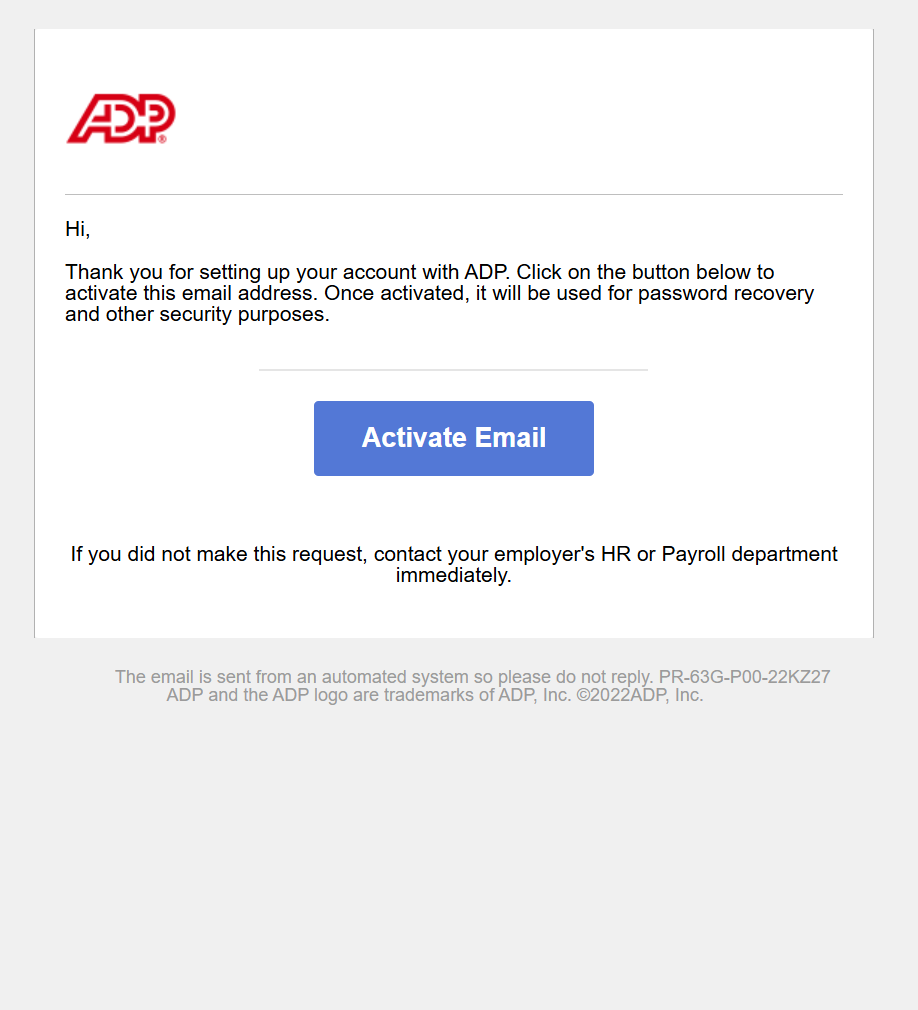
Email Templates
Initially used my basic knowledge of HTML to create simple email templates for testing purposes. Afterward, I leveraged raw text from emails I personally received and utilized ChatGPT to generate more advanced and consistently formatted HTML email templates, improving the efficiency and professionalism of my communications.
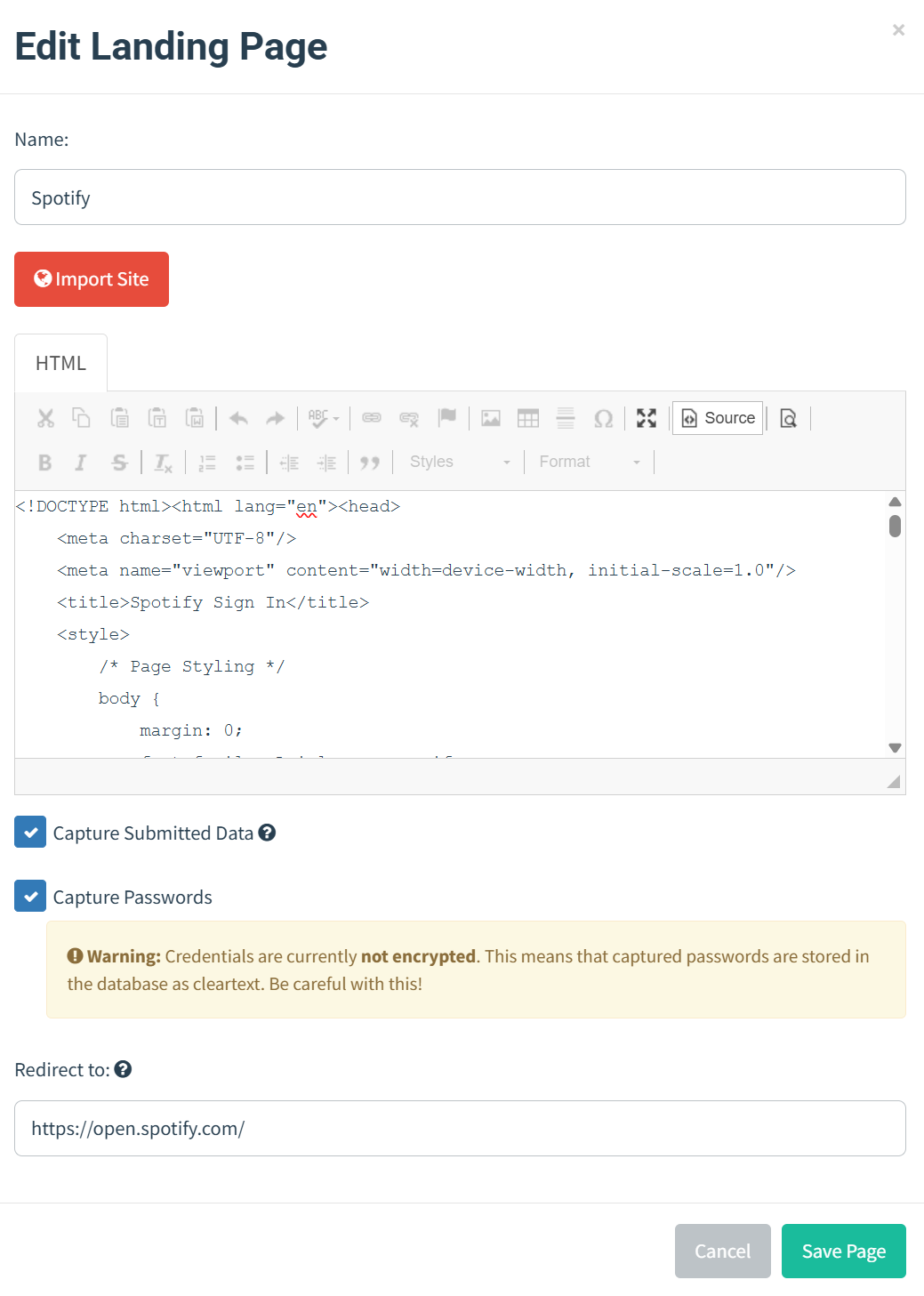
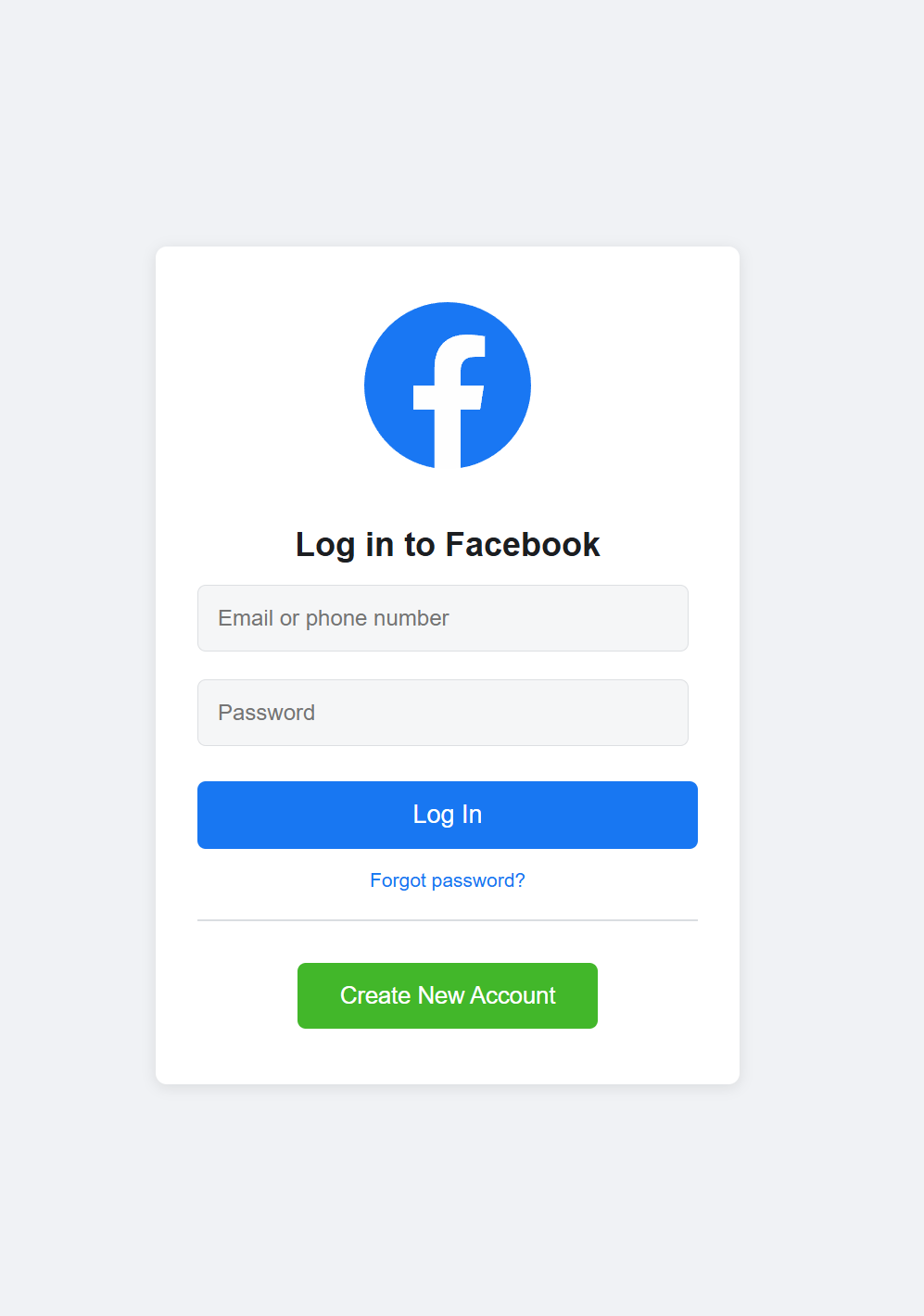
Landing Pages
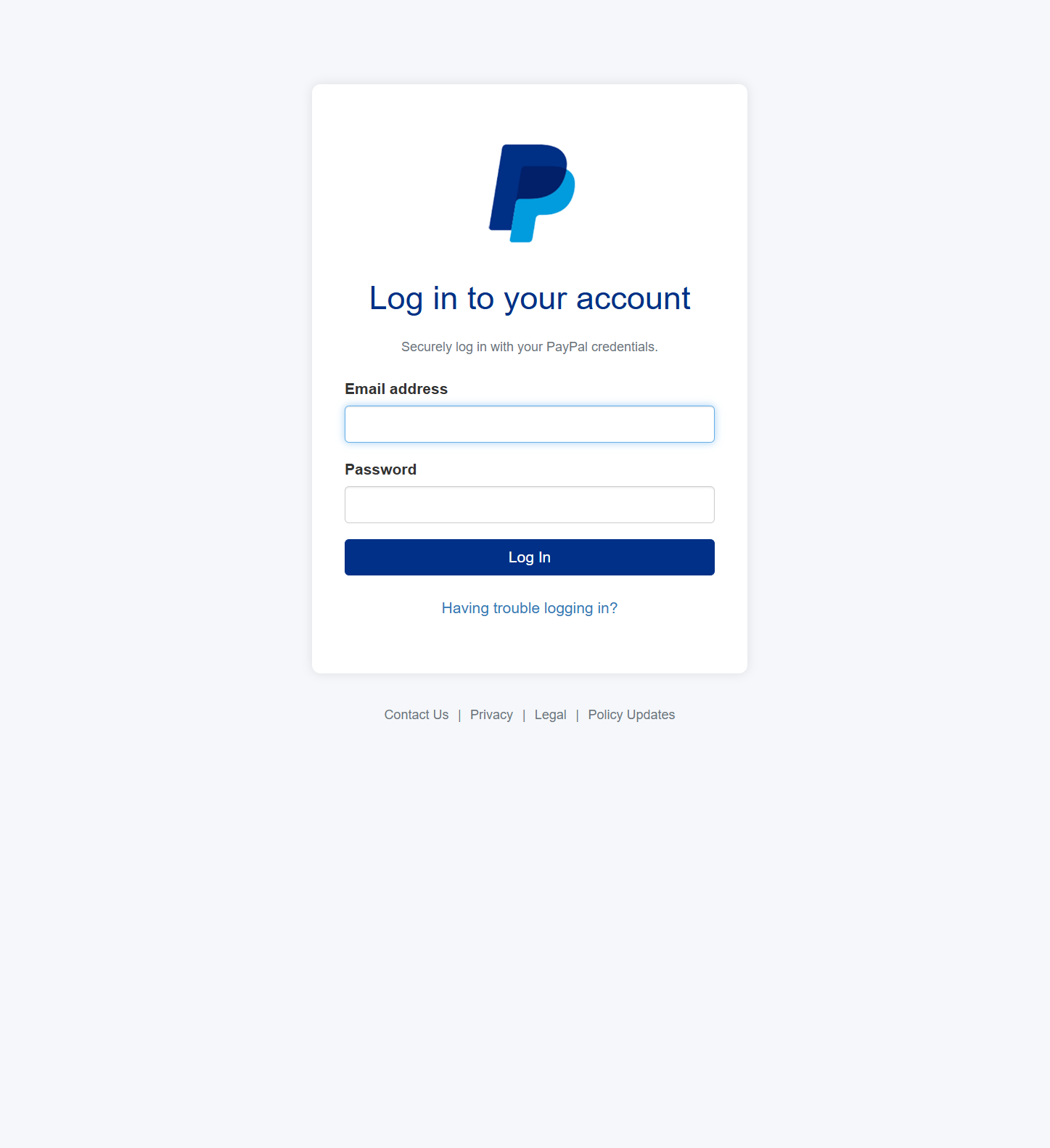
I created landing pages by importing existing website sign-in pages. Additionally, I used ChatGPT to generate similar login pages in HTML, allowing me to replicate and customize the design and functionality.
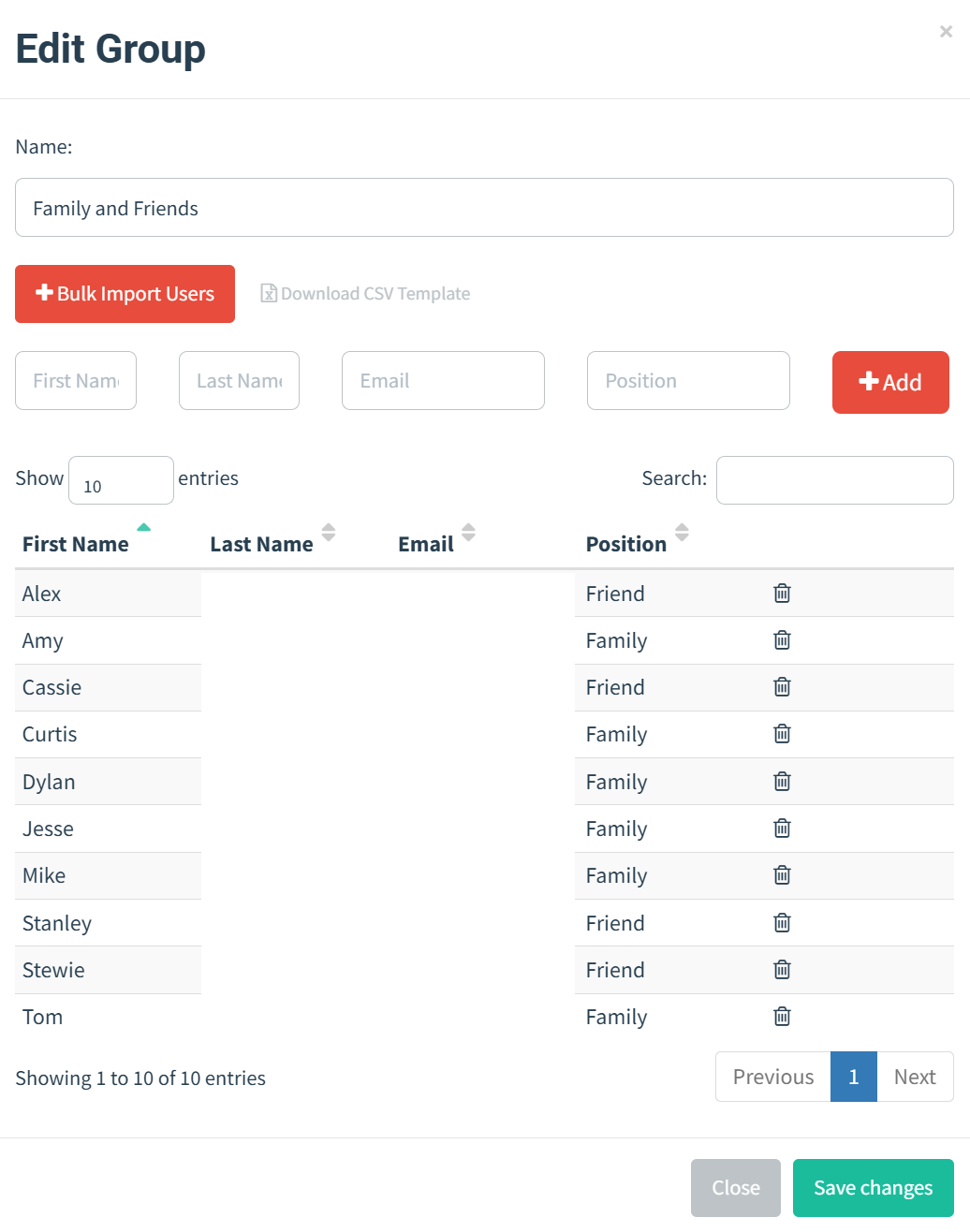
User & Groups
I contacted 10 individuals and obtained their full permission to participate in my phishing attack simulation. I collected their email addresses to include them in the campaign and used this information to send simulated phishing emails as part of the exercise.
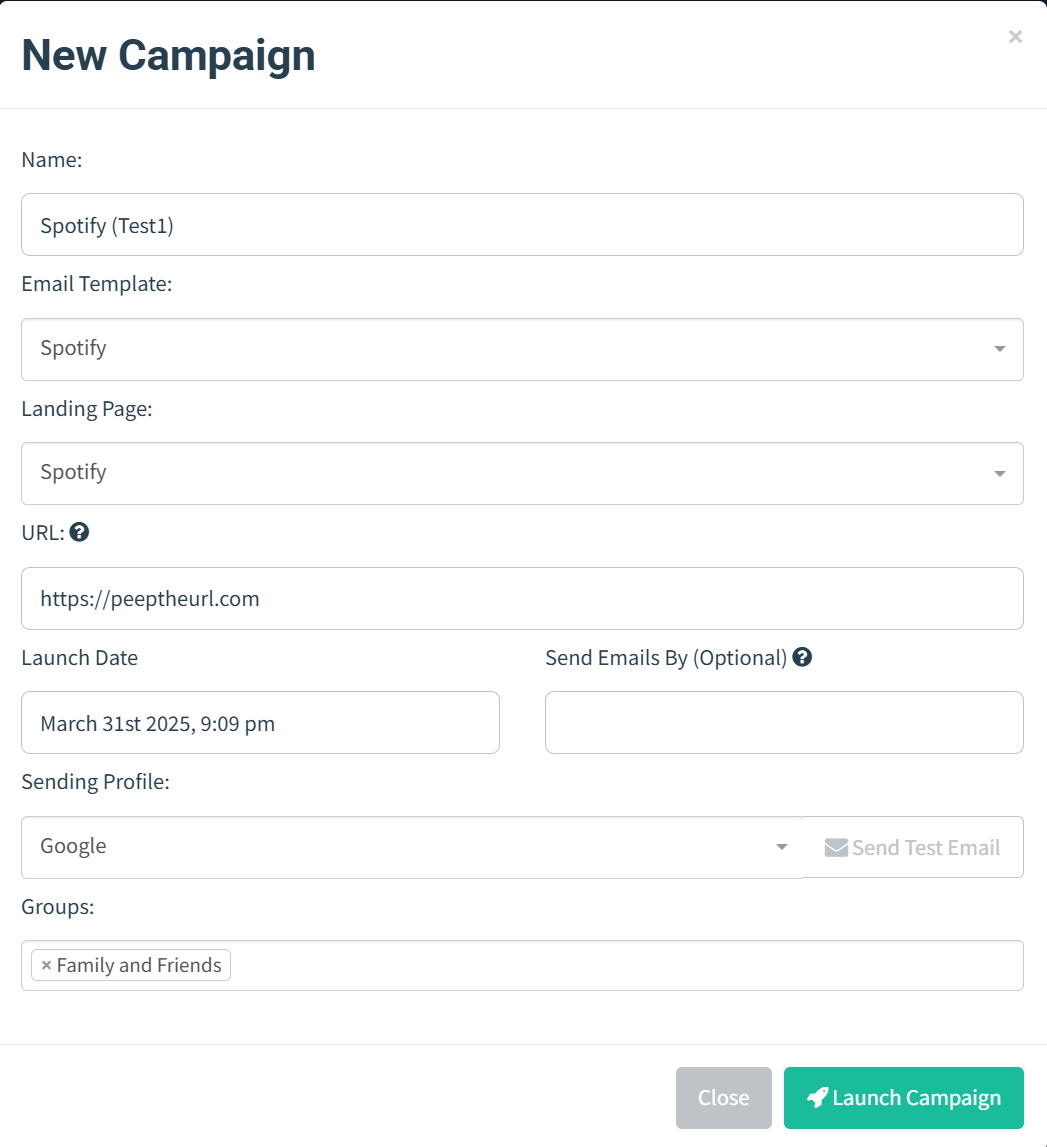
Deploy Campaign
I selected the appropriate email template and landing page for the campaign, identified the desired target group, and scheduled the launch date. To increase the likelihood of email delivery and avoid triggering spam filters, I strategically staggered the email distribution over several hours, ensuring the messages reached the intended recipients effectively.
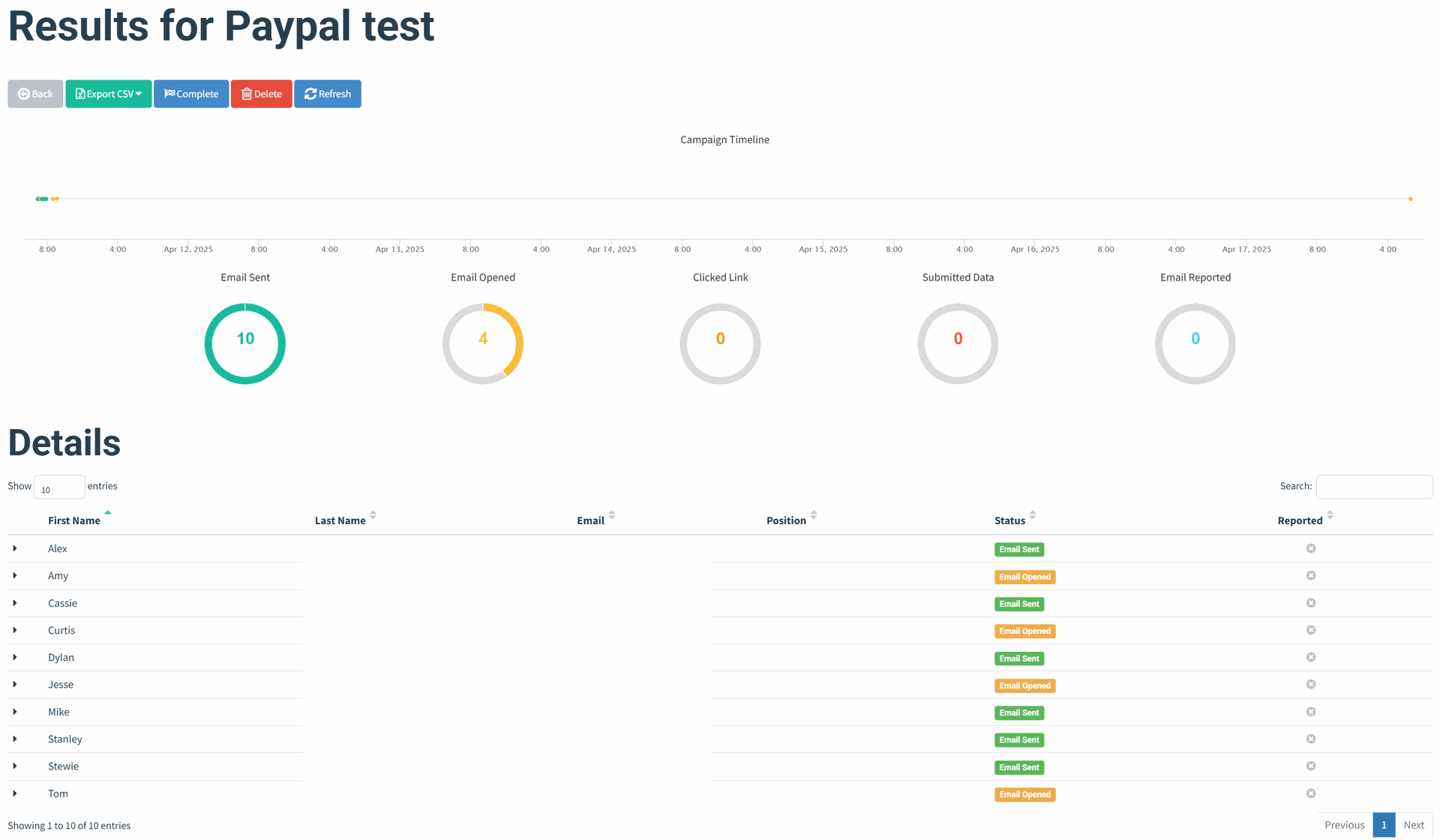
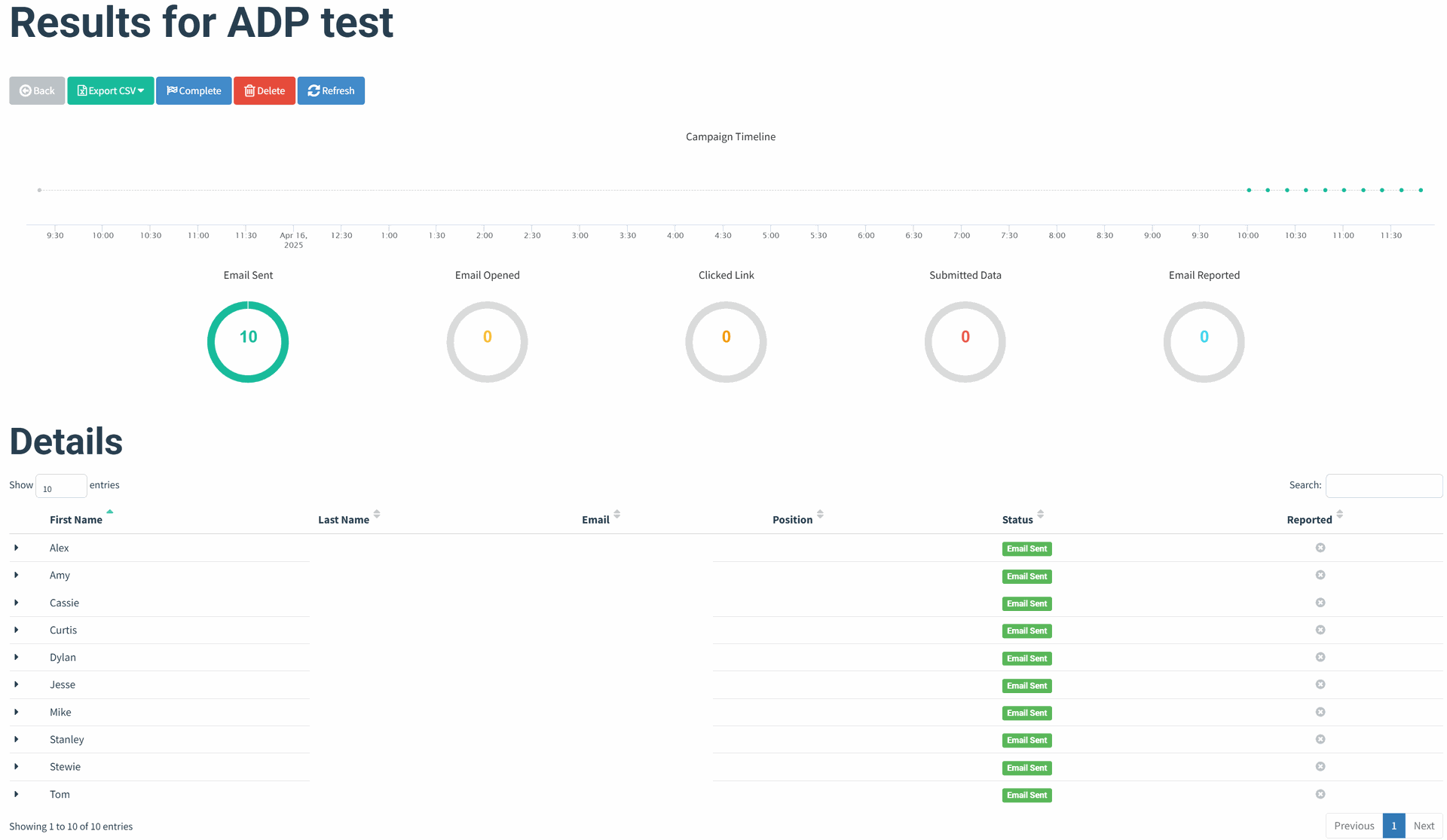
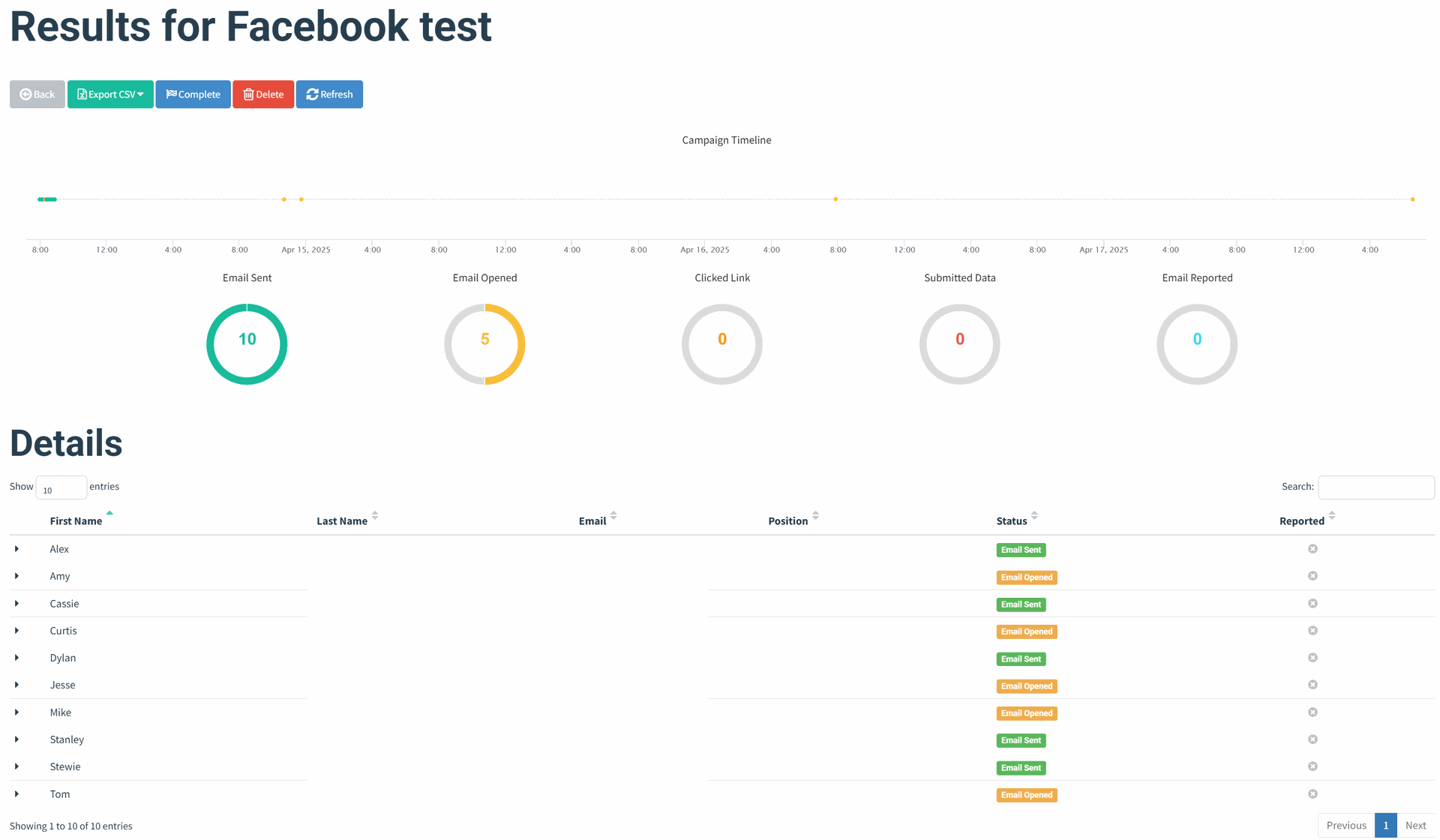
Results
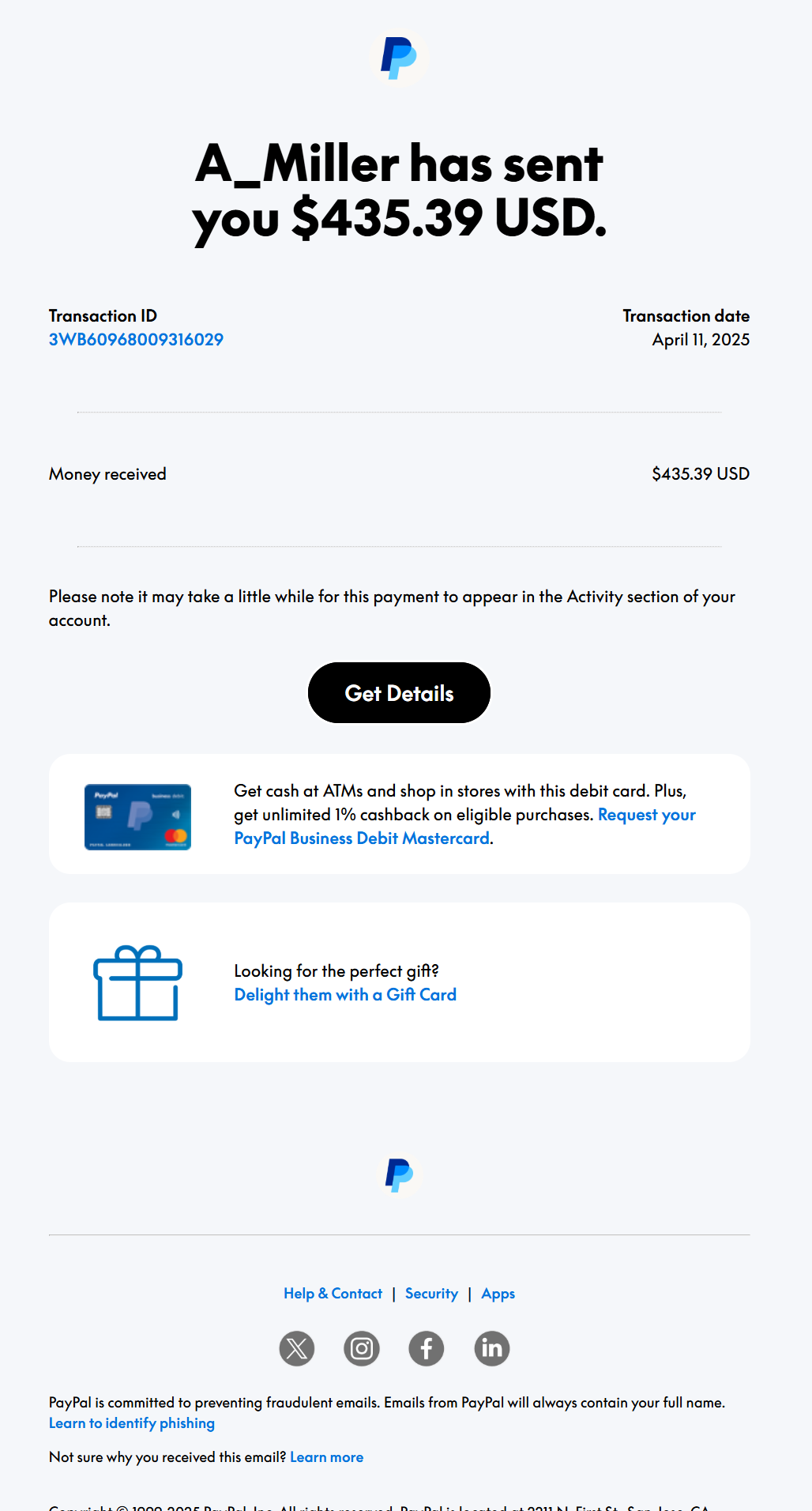
Email Template
Landing Page
Email Template
Landing Page
Email Template
Landing Page
Lessons Learned
This project was honestly a fun one to complete, not just because of the technical side, but also because of how it helped me better understand the mindset of an attacker.
Technical Takeaways:
- I learned how to deploy an instance on AWS, which was my first time spinning up a cloud-hosted server from scratch.
- I successfully linked a custom domain to the instance and even set it up for email functionality, which made the phishing campaign feel a lot more realistic.
- I also tackled SSL/TLS certificates, getting HTTPS up and running so the landing pages looked legit and didn’t trigger browser warnings. This was a big win from a social engineering standpoint.
Social Engineering Insights:
- I ran a few test campaigns with a small group. Interestingly, most users opened the emails, but none of them clicked on any links which says a lot about how important visual trust signals and link context are.
- Based on user feedback, most emails landed in inboxes, but a few were flagged as spam; useful info for understanding mail server reputation and deliverability.
The reason behind this project was personal as some friends and family had fallen victim to phishing scams, and I wanted to learn how these attacks are crafted to better protect others. It gave me valuable insight into how easy it can be to trick someone if you're not paying attention, and how attackers think when setting up a phishing attempt. I ended up stopping after three campaigns because the AWS usage costs started stacking up quickly. That said, even with the limited scope, I gained a ton of hands-on experience in both offensive tactics and defensive awareness.